Operating System theory explores the fundamental principles that drives the modern-day computer system. The key principles are Threads and process synchronization, Memory management, File systems, Mass storage, I/O, and Security and protection. These concepts enable the operating system to perform its functions.
Threads and process synchronization is the basis of how operations and instructions are executed in the CPU. These operations are managed in different CPU configurations by pipelining, threading and multi-threading. Modern computer systems are able to execute multiple programs concurrently within the CPU configuration and hardware constraints using these techniques.
Memory management is a critical component of operating systems that ensures efficient resource allocation, process isolation, and system performance optimization. The Memory Management Unit (MMU) is the hardware component that controls the flow of data through memory exchanges, primarily to convert virtual memory addresses to physical memory locations used by the computers RAM. Without the MMU controlling access of memory, processes would access the physical memory directly leading to data corruption, collisions, and security vulnerabilities.
The File system management component of the operating system is responsible for organizing, storing, retrieving, and protecting data and is a key component of the operating system. Its main functions are Directory management, file management, file access protection, storage management, directory performance management, and file reliability management. File directories can be designed in several ways to make data storage and access more efficient depending on the purpose of the system. Several common directory structures are Single-Level, Two-Level, Tree-Structure, Acyclic-Graph and General Graph directories.
The computer system uses Mass-Storage Structures to store data within the computer system. The operating system is responsible for scheduling incoming requests to save, delete, and update data in Storage. These requests made by the file and virtual memory systems use disk-scheduling algorithms to balance response time efficiency with request fairness. Three commonly used disk-queue ordering are FCFS (First-come-first-served), SSTF (Shortest-seek-time-first), and SCAN (sweeping the disk arm to scan the disk). The operating system manages storage access requests and is optimized to maximize processing efficiency.
I/O refers to device data input and output to control and process device data. Basic types of hardware I/O devices are Storage, Input, Output, and Communication. These hardware devices are integrated into the computer system and managed by the OS using software interfaces. I/O devices use both a hardware and software layer to access and control the device. The hardware layer includes physical components that detect input/output signals, and the software layer includes drivers and APIs that process and transmit 1) input for processing, or 2) output to the connected devices. These components are controlled by the OS to work together and allow external devices to integrate into the computer system.
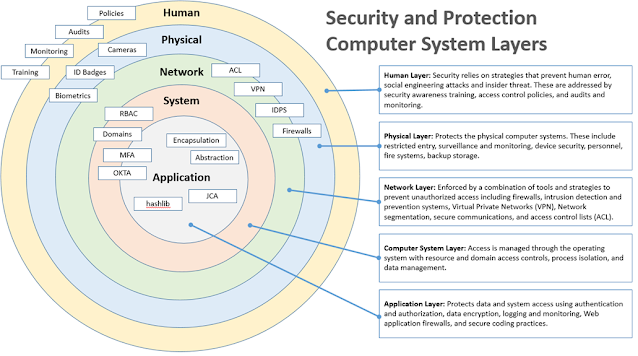
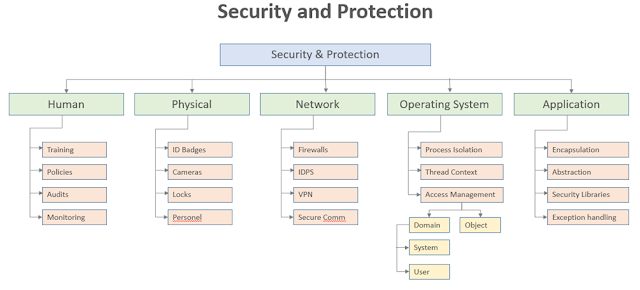
The computer system has layers of vulnerabilities and Protection and Security is implemented differently on each layer. The operating system manages access to the objects through resource and domain access controls, process isolation, and data management. These protections can be implemented using domain-based or language-based access management. Domain-based protection follows the concept of domain access management. Domain access is configured by grouping access levels for users, systems, or processes that need the same level of access. Language-based protection is managed in the applications codebase and uses high-level programming language features to enforce security and access control with built-in Classes and Data Types that can be used to protect data. Although the system isn’t capable of completely removing any risk of security breaches, using controls like these can mitigate the risk and secure the system.
Conclusion
These operating system features and concepts are the basis of designing software applications. In my current career, understanding these concepts better enables me to develop more efficient and secure software. As computing evolves, operating system theory continues to adapt, integrating emerging technologies such as distributed systems, real-time processing, and AI-driven automation will enhance efficiency, security, and scalability in modern computing environments.
References
Silberschatz, A., Galvin, P. B., & Gagne, G. (2014). Operating system concepts essentials (2nd ed.). Retrieved from https://redshelf.com
Coding Nijas (n.d.). Disk Scheduling Algorithm in OS (Operating System). (Naukri Code 360). Retrieved from https://www.naukri.com/code360/library/disk-scheduling-algorithms
Microsoft Azure (n.d.). What is a virtual machine (VM)?. Retrieved from Microsoft Azure website: https://azure.microsoft.com/en-us/resources/cloud-computing-dictionary/what-is-a-virtual-machine/?msockid=16a71c760c9d641607770e680dd165c7
Embedded (2024). Embedded Software Engineering Tools. Retrieved from Embedded.com: https://www.embedded.com/embedded-software-engineering-trends/
Multithreaded Crawler in Python. (2021, August 1). In GeeksforGeeks. Retrieved from GeeksforGeeks.org
Baatout, A. (2017, August 1). Multithreading vs. Multiprocessing in Python. Medium. Retrieved from medium.com
Sjoerd. (2010, June 15). Multiprocessing vs Threading Python. Stack Overflow. Retrieved from https://stackoverflow.com/questions/3044580/multiprocessing-vs-threading-python
MMU (Memory Management Unit) Wiki - (n.d.). Retrieved from https://www.fpgakey.com/wiki/details/351. (FPGAKey.com).
MMU Memory Management Unit, Chapter 14 (2014). Retrieved from: https://www.slideserve.com/ismet/mmu-memory-management-unit-chapter-14. (SlideServe.com)
Operating
system – Switching in Operating System. (n.d.). Retrieved from https://www.tutorialspoint.com/operating_system/os_context_switching.
(tutorialspoint.com)






Comments
Post a Comment